3 min read
Why your company needs end user security training
 Jake LaCaze
:
Published: May 13, 2022 Updated: October 1, 2024
Jake LaCaze
:
Published: May 13, 2022 Updated: October 1, 2024
The vast majority of security breaches are directly related to human error. After a phishing or emotet attack, the employee who enabled the attack may be terminated.
The vast majority of these employees likely were not given end user security training to avoid these disasters.
Lack of training amounts to negligence which hurts both the employee and the company.
Fortunately, there's a solution: end user security training.
What is end user security training?
End user security training is a formal process for educating employees about cybersecurity.
Formally training employees provides two benefits:
-
It guarantees that employees have been exposed to security training.
-
It increases the chances that employees are following the same practices.
The need for end user security training
Remote work has made preventing attacks more difficult. As workforces and data systems have become more spread out, companies have taken on more attack surface while combating more forms of threatware, giving threat actors more options to exploit. This change in the workforce has put more responsibility on a company's employees (end users), but many companies lag behind in terms of end user security training.
These days, a data breach can cost a business over $4 million.
Data breaches cost businesses in numerous ways, including:
-
Lost business share.
-
Loss of customers.
-
Lost revenue.
-
Increasing cost of acquiring new business due to diminished reputation.
Also, whether your company offers training—or the quality of training—may be a factor in your cyber liability insurance premiums. Insurance providers are asking about companies' training policies on the applications and weighing the quality of the answers.
These points show why end user security training is no trivial matter and should be a part of every company's managed security portfolio. Security is a team effort, not solely the responsibility of the IT department.
Why is educating end users important if my company already has security defense programs?
Email security tools reduce how many phishing emails get into users' inboxes. But bad emails will still get through. Even endpoint protection programs like next-generation antivirus aren't guaranteed to stop an attack.
At some point, protecting your network comes down to whether your employees click a bad link or open a malicious attachment. In this case, the buck stops with your employees.
Threat actors look for the easiest way in. And they often find it through a company's employees.
Companies often say that people are their most important asset. But untrained employees are a company's biggest security liability.
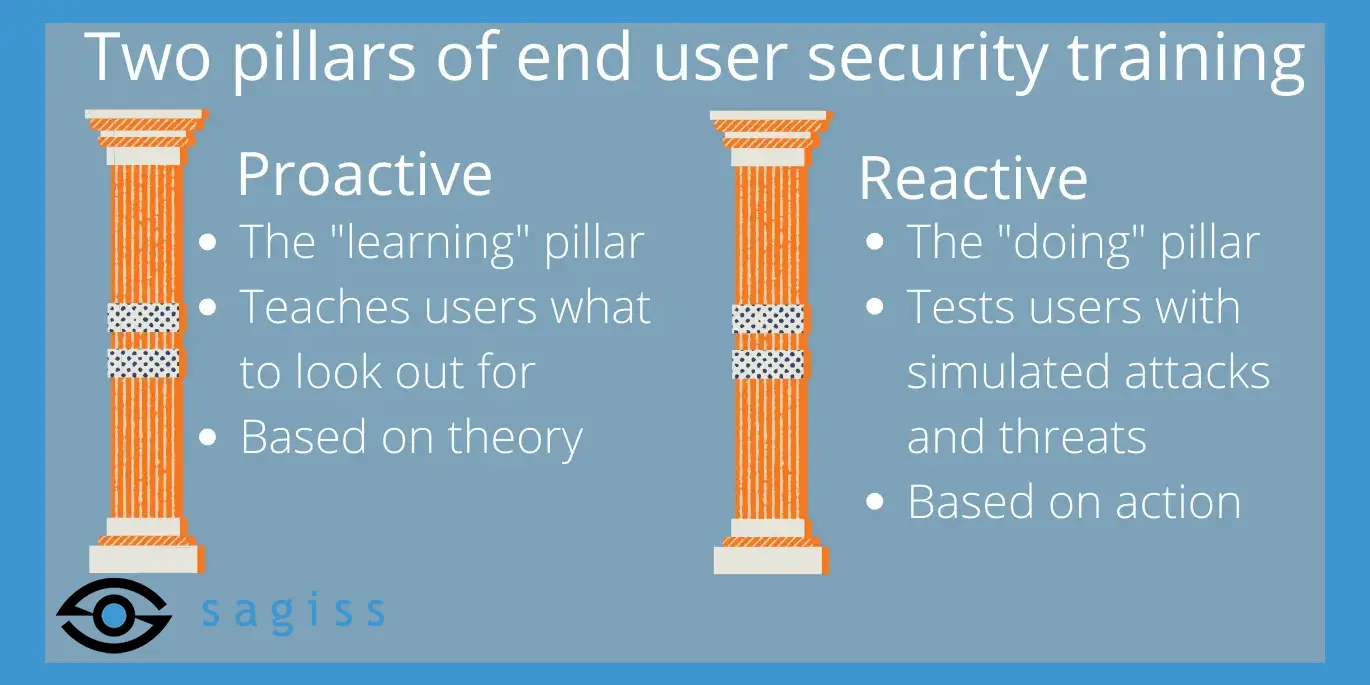
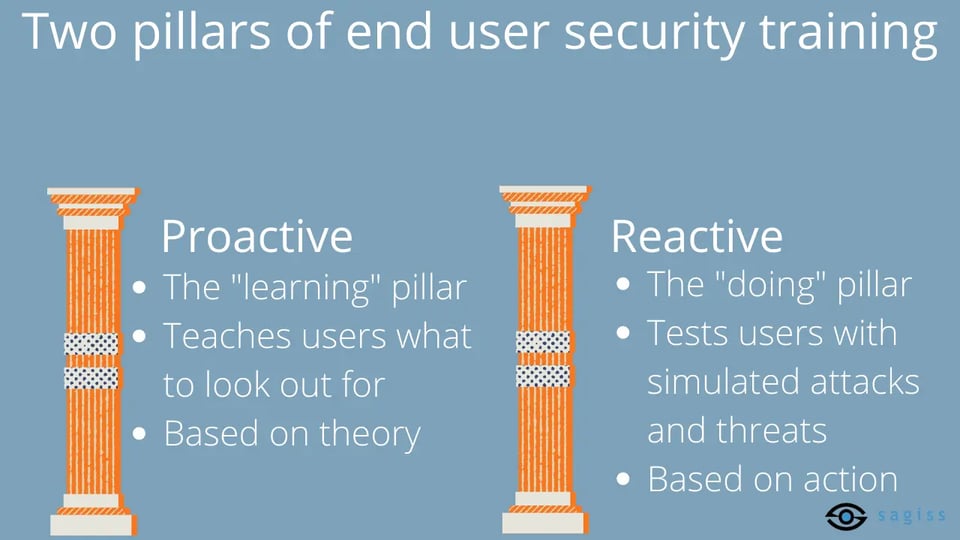
The two pillars of end user security training
End user security training is made up of two crucial elements:
-
The proactive element.
-
The reactive element.
The proactive element
The proactive element of end user security training is the pillar focused on classroom learning by educational materials including:
-
Videos.
-
Articles.
-
Infographics.
This is where end users are prepped on what to look out for and what to do when they come across materials from threat actors.
The proactive element is one of the most overlooked aspects of security. Businesses benefit from being more proactive, including using vulnerability management to identify security risks before they be can be exploited. By using a proactive element in its end user security training, your company is identifying potential risks before they have the chance to bring your business to its knees.
The reactive element
The reactive element of end user security training is the pillar focused on practice and how end users respond to threats by simulating attacks.
The most common form of attack simulation comes through email security testing, when employees are sent simulated phishing attempts.
To be effective, these simulated attacks should be:
-
Challenging: The simulations are best when they require end users to think before they click.
-
Continuous: The simulations cannot be a one-time thing.
-
Persistent: The simulations should take place at different times.
End user security training identifies struggling employees. Then you know where to focus education efforts to prevent an attack.
A chain is only as strong as its weakest link. You can't know the weakest link of your security chain if you don't test your employees.
Make end user security training part of your security portfolio today
Good security should be a habit for every company. Unfortunately, most people have horrible security practices they bring to the workplace, putting their employers' data and systems at risk.
To improve, end users first need proper education, which must be followed up with actual practice.
This is why end user security training is the best way to empower a company's workers and to reduce the odds of devastating attacks.
